by Karlene Lukovitz @KLmarketdaily
Source: www.mediapost.com, November 2022
Looking to exploit new Twitter owner Elon Musk’s declaration that the platform may start charging users for “verified” status and membership in the platform’s premium Blue service, cyber criminals are bombarding those users with scams.
“This presents a considerable financial and brand damage risk to organizations,” comments Matt Chiodi, chief trust officer of applications security platform Cerby. “Social media accounts are generally managed by marketing teams and can have access to hundreds of millions of corporate dollars for advertising. Not only could criminals siphon off that cash, they could defame a company’s Twitter profile with offensive content.”
Verified users are being hit with phishing attempts masquerading as notices from Twitter Services on their email accounts and on Twitter itself, according to posts by users and tech security media and experts.
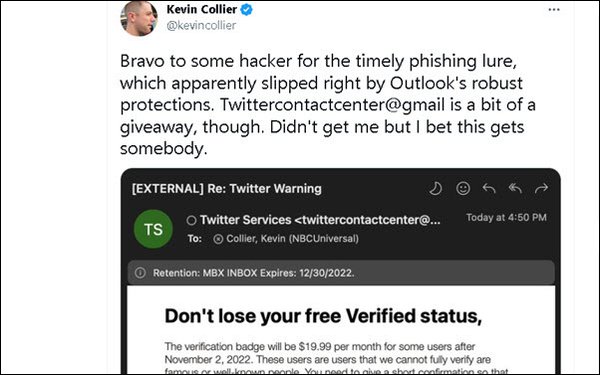
“Bravo to some hacker for the timely phishing lure, which apparently slipped right by Outlook’s robust protections,” tweeted NBC News reporter Kevin Collier (above). “Twittercontactcenter@gmail is a bit of a giveaway, though. Didn’t get me but I bet this gets somebody.”
The scam emails attempt to get recipients to click on a link that will supposedly confirm their identities and keep them from losing their verified status.
Others have received messages on the Twitter site that claim to be a “removal notice.” The posts claim that the recipient’s status has been identified as inauthentic, and that the account holder must follow the link and file an appeal or their blue-badge status may be permanently removed within 24 hours.
“Attackers capitalize on high profile, chaotic events and changes to drive pretext for lures likes this,” Bugcrowd founder Casey Ellis told InfoSecurity. “This campaign is a reminder that it doesn’t need to be a hurricane, a pandemic, or other kind of calamity to trigger this kind of attacker behavior. I recommend using multi-factor authentication and ‘think twice, click once’ to help mitigate this.”
“The security industry and big tech need to do a better job at making security automatic,” stresses Cerby’s Chiodi. “For too long, we’ve blamed users for poor practices like clicking on phishing links. We haven’t learned that no matter the amount of security training, users aren’t the problem; it’s the technology we’ve created for them.
“None of the prominent social media platforms offer enterprise-grade authentication options to their billions of business and professional users,” he continues. “This is unacceptable for tools so widely used by consumers and critical to enterprises and democracy. These ‘unmanageable applications’ do not support security standards such as single sign-on or automated user creation and removal through a standard known as SCIM… it’s one of the main reason criminals go after social accounts.
“Phishing will continue to grow until the world moves to passwordless,” Chiodi concludes. “Passwords aren’t the problem; it’s how users manage them since they have traditionally had no options to help automate the entire process from account creation to login. Two ways to solve this are security and privacy settings that are secure by default and automation.”